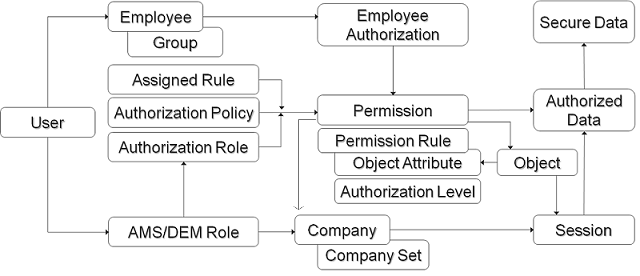
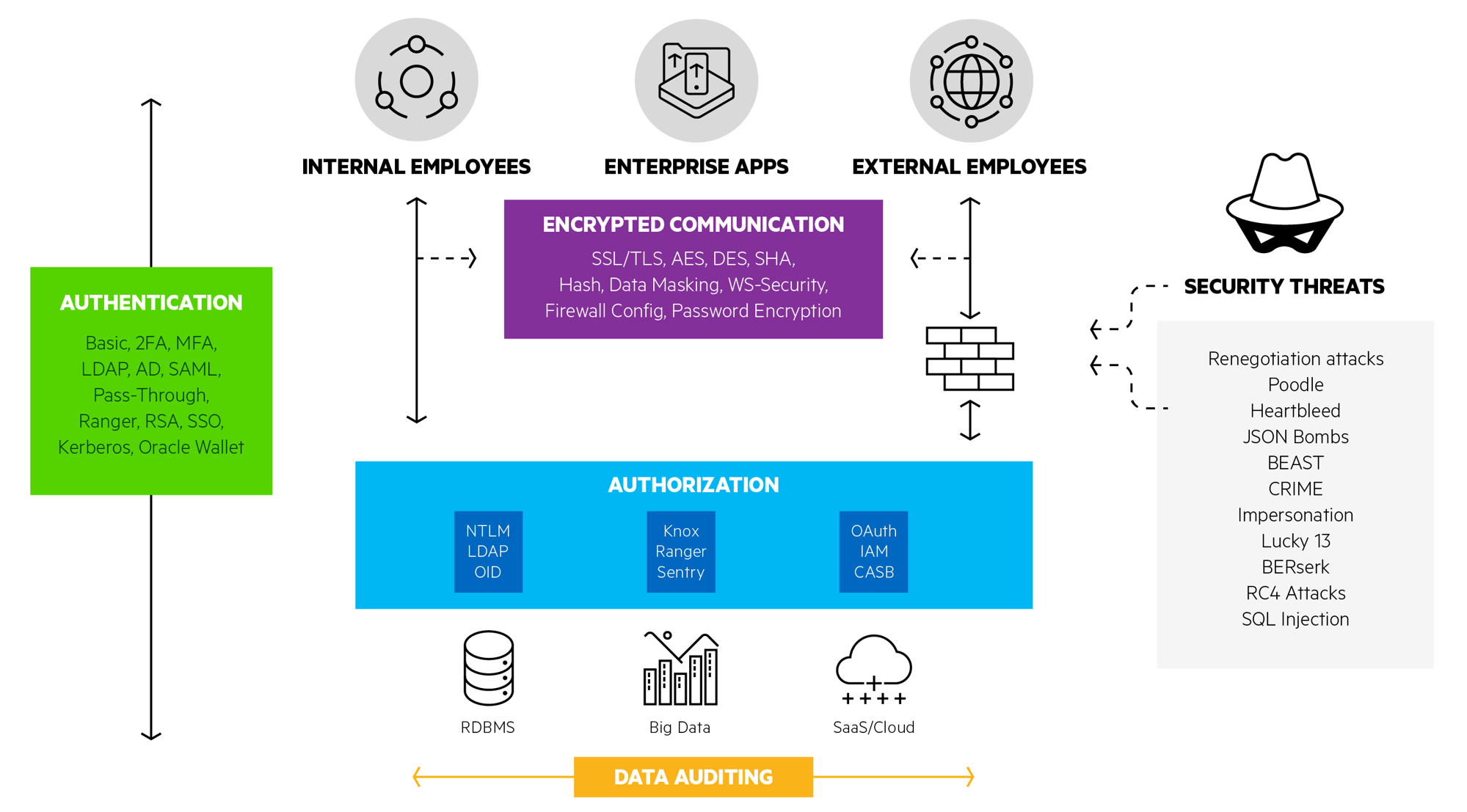
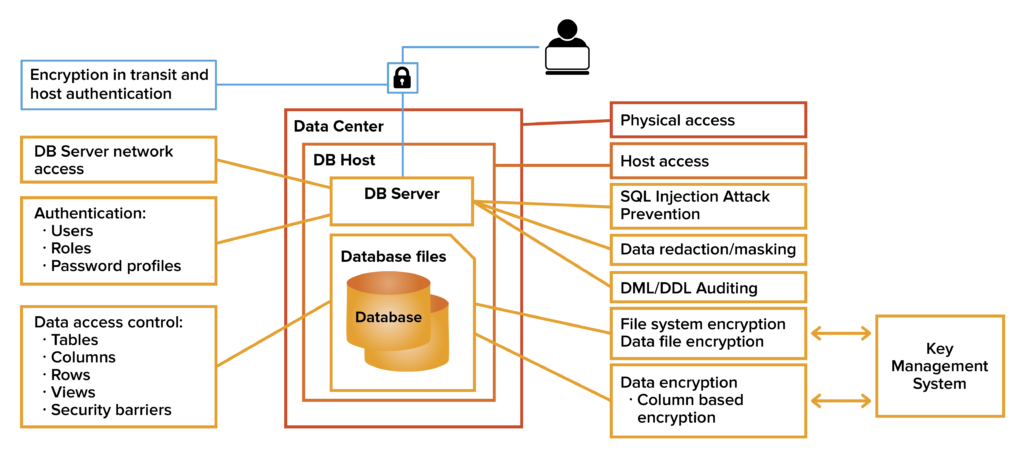
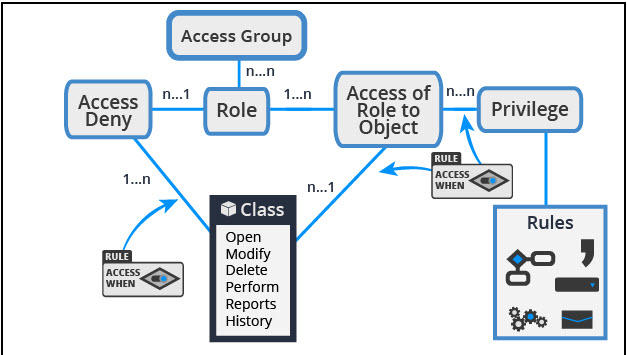
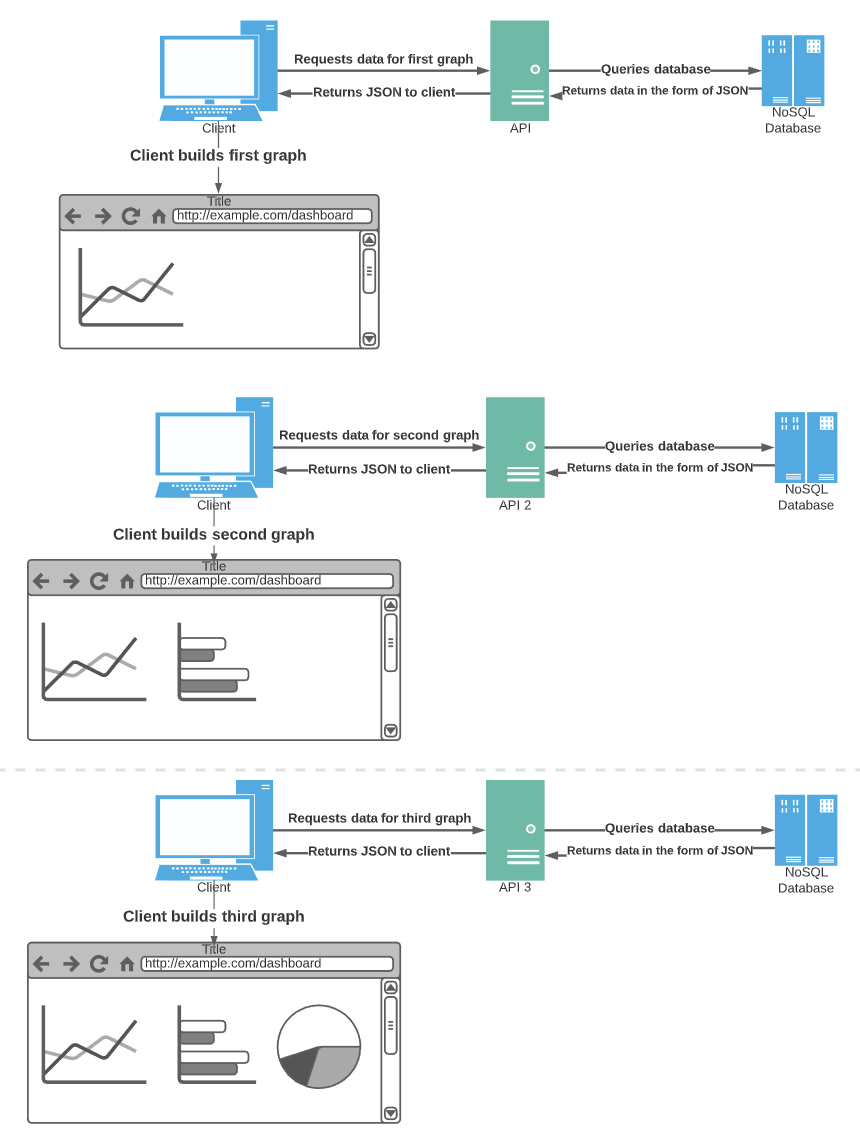
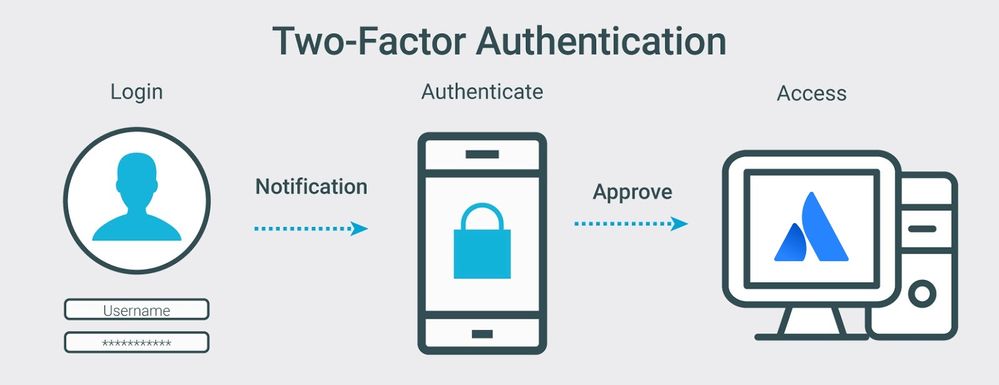
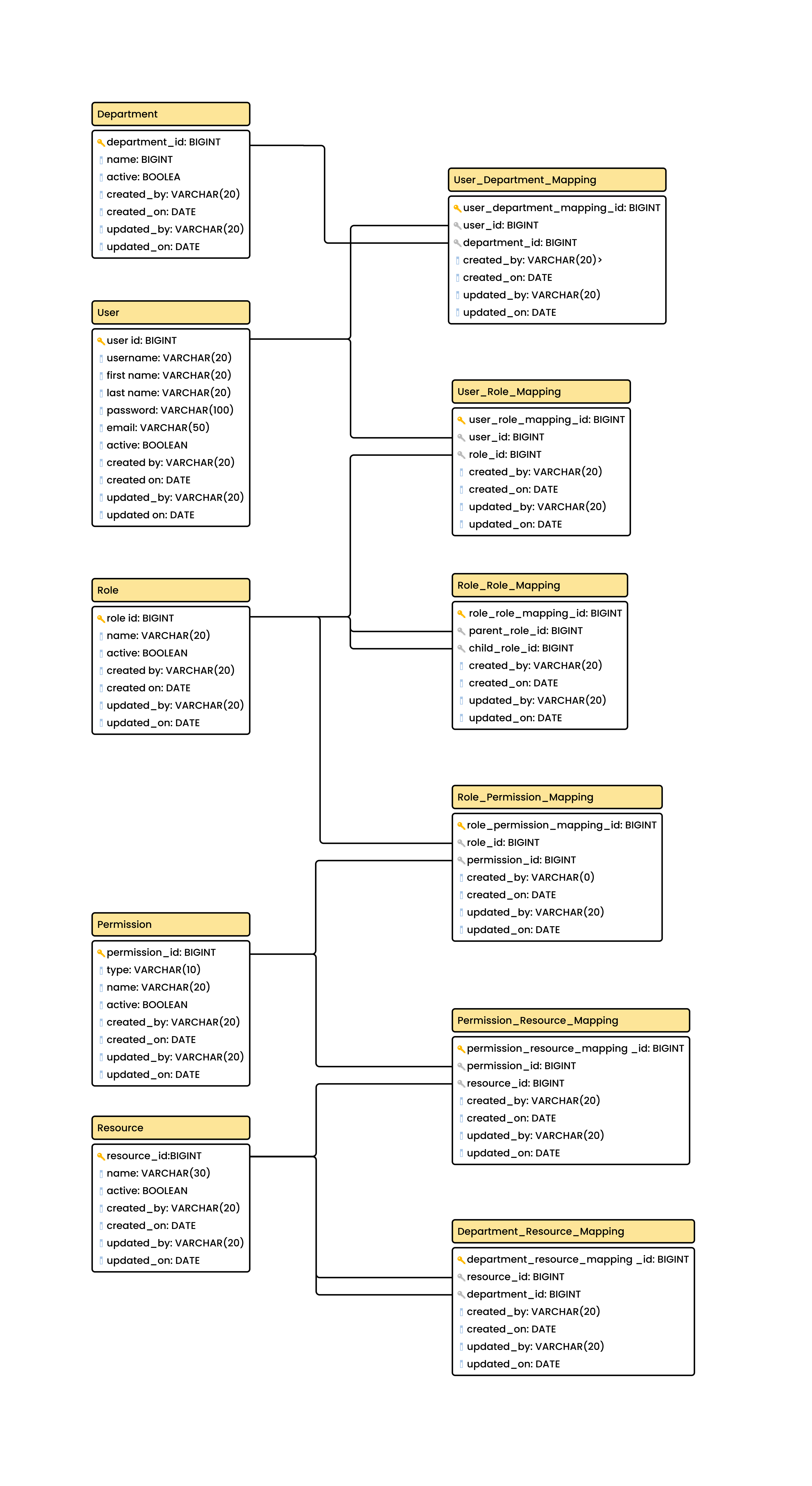
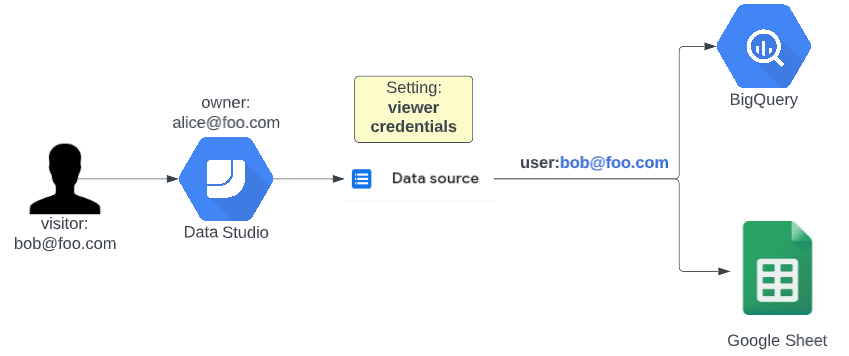
Subsurface Data Management: Overview of authentication and authorization on AWS implementation of OSDU™ Data Platform | AWS for Industries

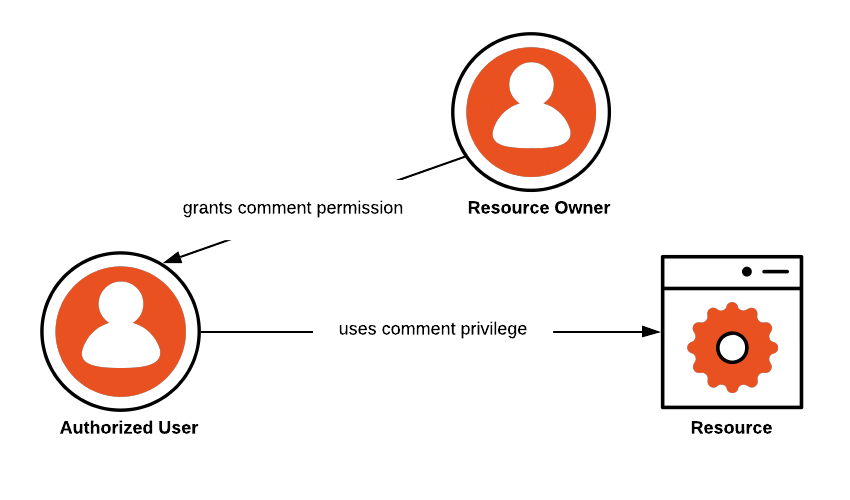
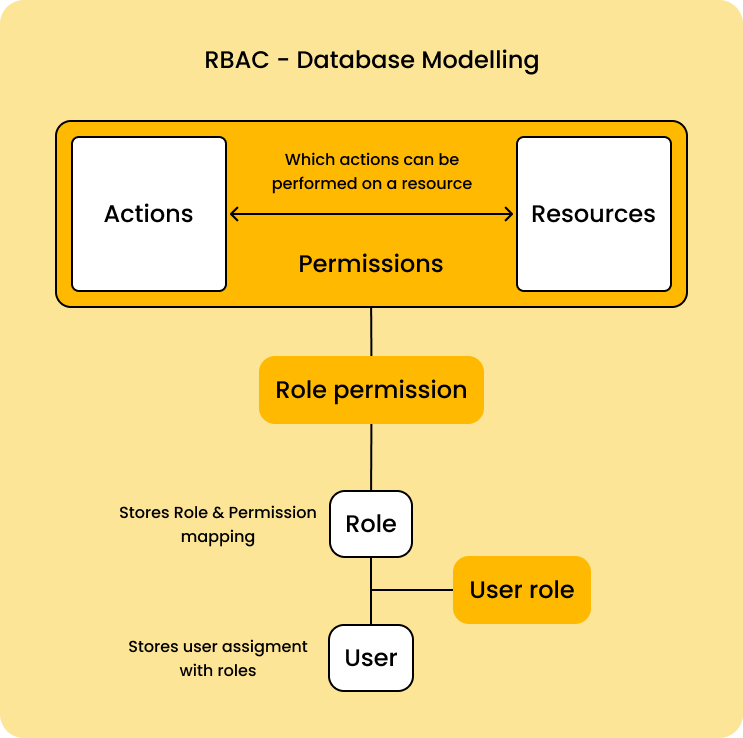
How to scale your authorization needs by using attribute-based access control with S3 | AWS Security Blog