
An efficient hybrid hash based privacy amplification algorithm for quantum key distribution | SpringerLink
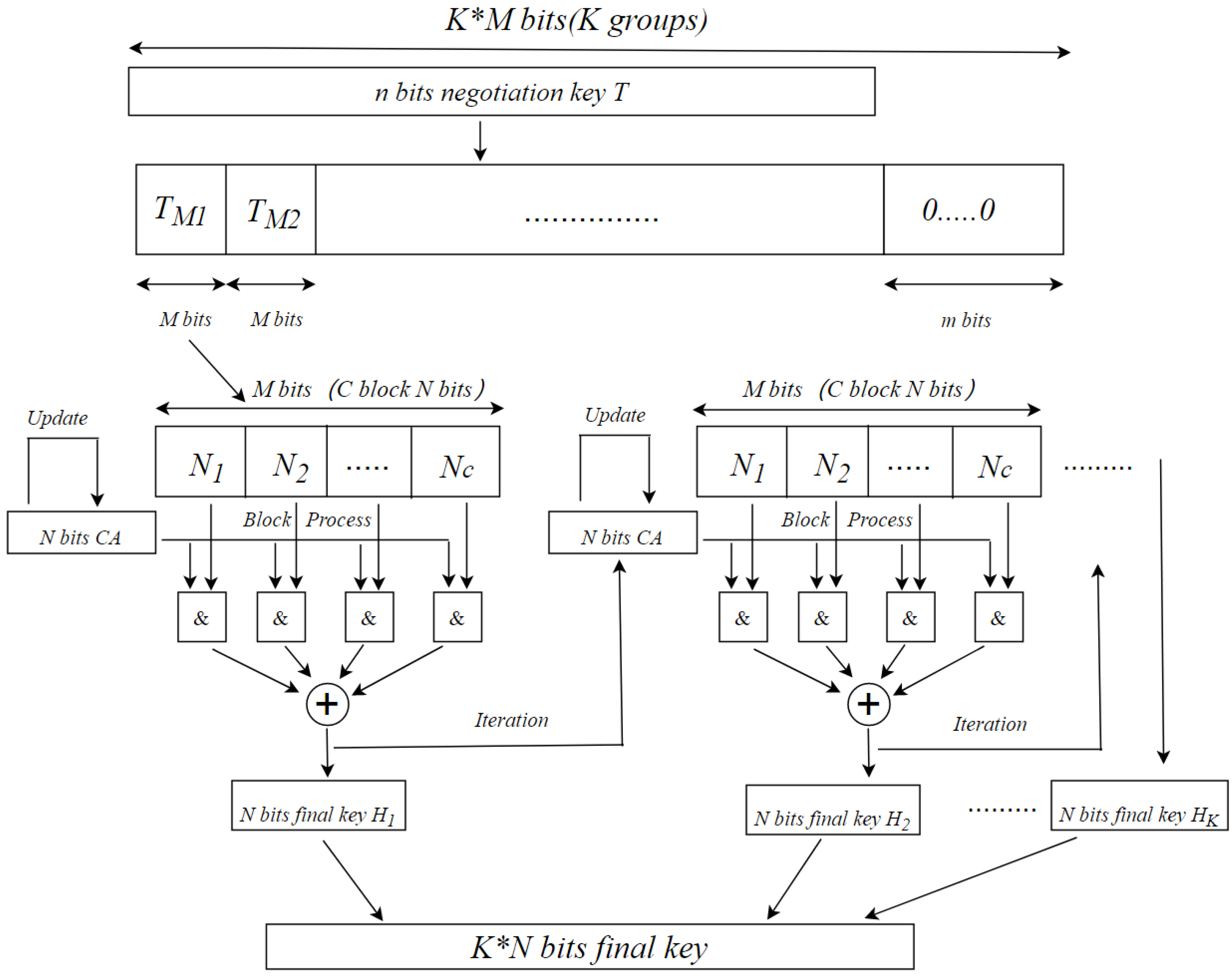
Electronics | Free Full-Text | High-Speed Privacy Amplification Algorithm Using Cellular Automate in Quantum Key Distribution
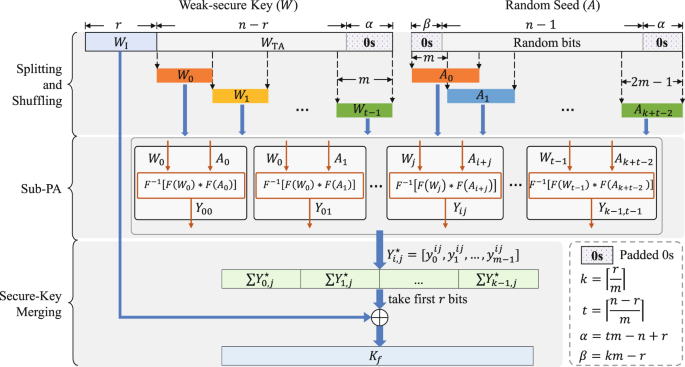
High-speed and Large-scale Privacy Amplification Scheme for Quantum Key Distribution | Scientific Reports

Pre-Privacy Amplification: A Post-Processing Technique for Quantum Key Distribution with Application to the Simplified Trusted Relay
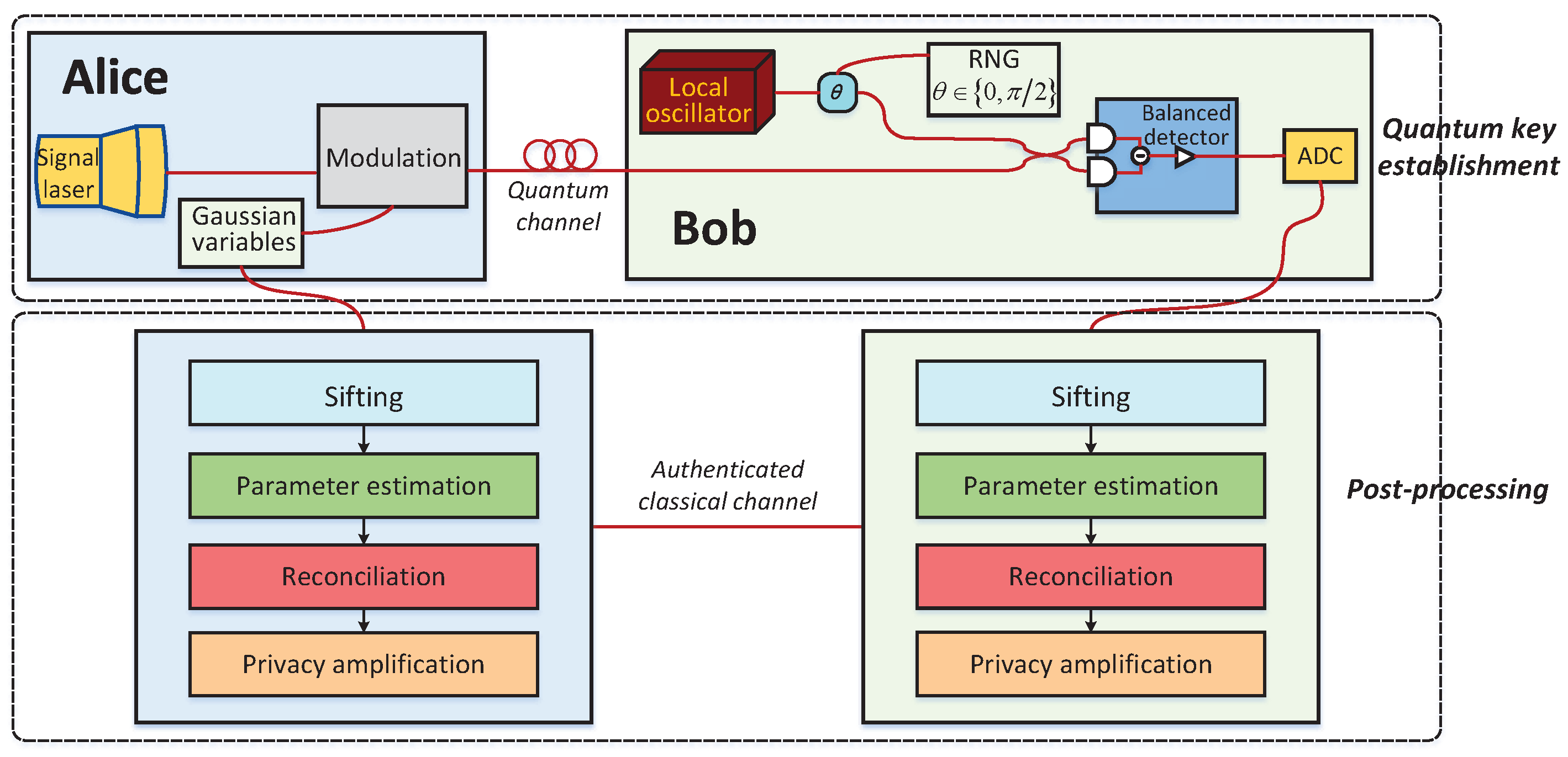
Entropy | Free Full-Text | An Improved Slice Reconciliation Protocol for Continuous-Variable Quantum Key Distribution
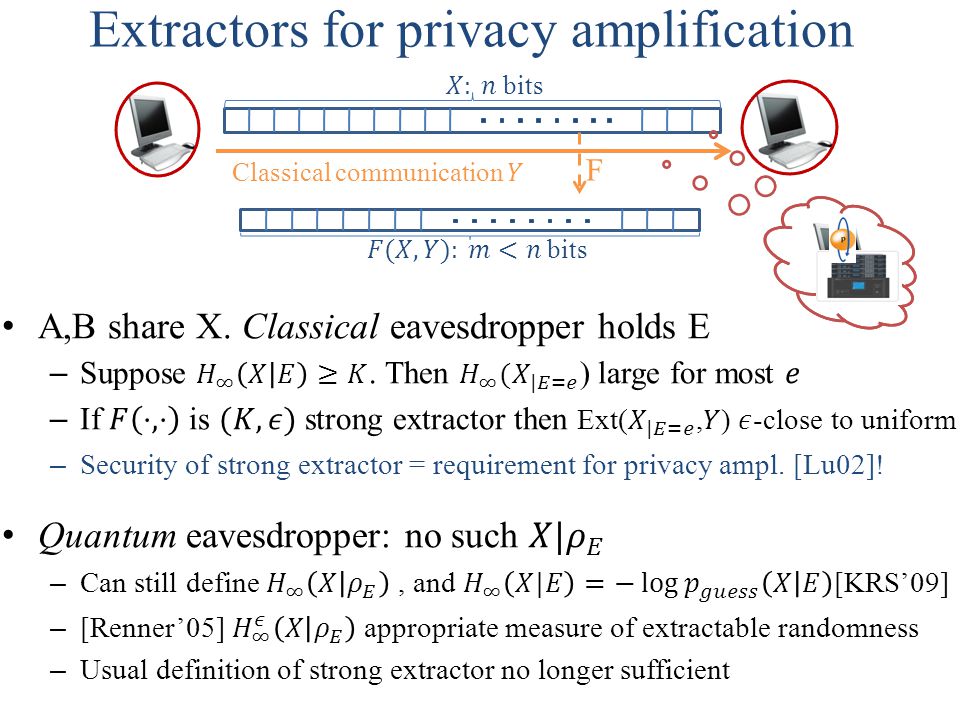
Randomness Extraction and Privacy Amplification with quantum eavesdroppers Thomas Vidick UC Berkeley Based on joint work with Christopher Portmann, Anindya. - ppt download

Privacy Amplification with Couplings and Overlapping Mixtures | Rafik Hariri Institute for Computing and Computational Science & Engineering
![PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5ab3cb538f80f4bbf539103464fe597ba2d93a7c/1-Figure1-1.png)
PDF] High-Speed Privacy Amplification Scheme Using GMP in Quantum Key Distribution | Semantic Scholar

PPT - Randomness Extraction and Privacy Amplification with quantum eavesdroppers PowerPoint Presentation - ID:4846836

Differences between Extractors and Privacy Amplification for Quantum Random Generators - Cryptography Stack Exchange
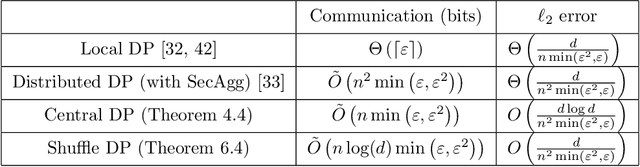
Privacy Amplification via Compression: Achieving the Optimal Privacy-Accuracy-Communication Trade-off in Distributed Mean Estimation: Paper and Code - CatalyzeX

![PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar PDF] Privacy Amplification via Random Check-Ins | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a86aa46da4bcf1daef2e88b7656b7c8477db8e0f/2-Figure1-1.png)






